Unauthrized Data Rollbak Or Undo Cia Triad
Muz Play
Mar 31, 2025 · 6 min read
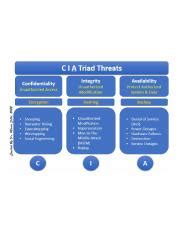
Table of Contents
Unauthorized Data Rollback or Undo: A CIA Triad Vulnerability
The unauthorized rollback or undo of data represents a significant vulnerability within the CIA triad (Confidentiality, Integrity, Availability). While often overlooked, this threat can severely compromise all three pillars of information security, leading to substantial financial losses, reputational damage, and legal repercussions. This article delves deep into the nature of unauthorized data rollbacks, exploring its various forms, underlying causes, and effective mitigation strategies.
Understanding the CIA Triad in the Context of Data Rollback
The CIA triad provides a fundamental framework for information security. Let's examine how unauthorized data rollbacks impact each element:
-
Confidentiality: Rollback attacks can expose sensitive data that was previously considered confidential. Imagine a scenario where an unauthorized user rolls back a database to a previous state, revealing deleted or modified confidential client information, financial records, or intellectual property. This directly violates the principle of confidentiality.
-
Integrity: Data integrity is compromised when unauthorized rollbacks alter the officially accepted version of data. The rolled-back data may be outdated, inaccurate, or maliciously modified, leading to inconsistencies and flawed decision-making. This undermines the trust placed in the data's accuracy and reliability.
-
Availability: While seemingly less direct, unauthorized rollbacks can significantly affect data availability. A malicious rollback can render critical systems or data inaccessible, disrupting operations and causing significant downtime. This is especially critical for organizations that rely on real-time data processing and transactions.
Types of Unauthorized Data Rollbacks
Unauthorized data rollbacks can manifest in several forms, each with its unique characteristics and implications:
1. Malicious Rollbacks:
This involves a deliberate attempt by a malicious actor (internal or external) to revert data to a previous state to achieve a specific goal. Motives can range from data theft and manipulation to sabotage and extortion. For instance, an insider might roll back data to cover up fraudulent activities or an external attacker might roll back a database to erase audit logs of their intrusion.
2. Accidental Rollbacks:
These are unintentional actions that occur due to human error or system malfunctions. An administrator might accidentally rollback data during a routine maintenance procedure, or a system glitch could trigger an unintended data rollback. While not malicious, these accidental rollbacks still pose significant risks.
3. Exploiting System Vulnerabilities:
Sophisticated attackers might exploit vulnerabilities in database management systems (DBMS) or backup/recovery mechanisms to initiate unauthorized rollbacks. This often involves exploiting known vulnerabilities or leveraging zero-day exploits to gain unauthorized access and control over data rollback capabilities.
4. Insider Threats:
Employees with sufficient privileges (e.g., database administrators, system administrators) could misuse their access rights to perform unauthorized data rollbacks. This could be driven by malicious intent or negligence, highlighting the importance of robust access control and monitoring.
Root Causes of Unauthorized Data Rollbacks
Understanding the root causes is crucial for effective mitigation. Here are some key factors contributing to unauthorized data rollbacks:
-
Weak Access Control: Insufficient access control mechanisms allow unauthorized individuals to access and manipulate data rollback functionalities. This often stems from poorly defined roles and responsibilities, inadequate privilege management, and a lack of proper authentication and authorization.
-
Lack of Audit Trails: Without comprehensive audit trails, tracking unauthorized data rollbacks becomes extremely difficult. The absence of logs documenting who accessed rollback functionality, when it was accessed, and what changes were made renders investigations nearly impossible.
-
Insufficient Monitoring: Inadequate monitoring of system activity and user behavior can allow unauthorized data rollbacks to go undetected. Real-time monitoring and alerting systems are crucial for promptly identifying suspicious activity.
-
Vulnerable Systems: Outdated or poorly configured systems are more susceptible to exploitation, allowing attackers to gain unauthorized access and trigger data rollbacks. Regular patching, security updates, and robust configuration management are essential.
-
Inadequate Backup and Recovery Procedures: Poorly designed or poorly implemented backup and recovery procedures can create opportunities for unauthorized data rollbacks. This includes a lack of version control, insufficient security around backup storage, and ineffective recovery mechanisms.
Mitigating the Risk of Unauthorized Data Rollbacks
Implementing a multi-layered security approach is critical to mitigating the risks associated with unauthorized data rollbacks. This should encompass the following measures:
1. Robust Access Control and Privilege Management:
- Principle of Least Privilege: Grant users only the minimum necessary privileges to perform their job duties. Avoid granting excessive access to data rollback functionalities.
- Role-Based Access Control (RBAC): Implement RBAC to define roles and assign specific permissions based on roles, limiting unauthorized access.
- Multi-Factor Authentication (MFA): Implement MFA to enhance the security of user accounts and prevent unauthorized access.
2. Comprehensive Audit Trails and Logging:
- Detailed Logs: Maintain detailed logs of all data access, modifications, and rollback attempts. These logs should include timestamps, user identities, and specific actions taken.
- Regular Log Review: Regularly review audit logs to detect any suspicious activity or unauthorized rollbacks.
- Secure Log Storage: Store logs securely to prevent unauthorized alteration or deletion.
3. Real-time Monitoring and Alerting:
- Security Information and Event Management (SIEM): Implement SIEM systems to collect, analyze, and correlate security logs from various sources.
- Intrusion Detection/Prevention Systems (IDS/IPS): Utilize IDS/IPS to detect and prevent malicious activities, including unauthorized data rollbacks.
- Anomaly Detection: Implement anomaly detection algorithms to identify unusual patterns of access and data modifications that may indicate unauthorized rollbacks.
4. Secure Backup and Recovery Procedures:
- Version Control: Implement robust version control for backups, allowing for easy tracking and restoration of specific versions.
- Secure Backup Storage: Store backups securely, using encryption and access control to prevent unauthorized access or modification.
- Regular Backup Testing: Regularly test backup and recovery procedures to ensure they function as intended.
- Immutable Backups: Consider using immutable backups that cannot be altered or deleted once created.
5. Regular Security Assessments and Penetration Testing:
- Vulnerability Scanning: Regularly scan systems for vulnerabilities that could be exploited to perform unauthorized data rollbacks.
- Penetration Testing: Conduct regular penetration testing to simulate real-world attacks and identify weaknesses in security controls.
- Security Audits: Conduct regular security audits to assess the effectiveness of existing security controls and identify areas for improvement.
6. Employee Training and Awareness:
- Security Awareness Training: Educate employees about the risks associated with unauthorized data rollbacks and the importance of following security protocols.
- Data Handling Policies: Develop and enforce clear data handling policies that outline proper procedures for accessing, modifying, and managing data.
Conclusion: Proactive Security is Paramount
Unauthorized data rollbacks pose a significant threat to data integrity, confidentiality, and availability. By implementing a comprehensive security strategy that addresses access control, audit trails, monitoring, secure backups, and employee training, organizations can significantly reduce their risk exposure. A proactive and multi-faceted approach is crucial to safeguarding data and maintaining business continuity in the face of increasingly sophisticated cyber threats. Remember that continuous vigilance and adaptation to evolving threats are essential for maintaining robust information security. Failing to address this vulnerability can result in severe consequences, impacting not just technical systems, but also an organization's reputation, financial stability, and legal standing.
Latest Posts
Latest Posts
-
Why Is Water Necessary For Life
Apr 02, 2025
-
The Process Of Independent Assortment Refers To
Apr 02, 2025
-
Is Table Salt Homogeneous Or Heterogeneous
Apr 02, 2025
-
What Part Of Bacteria Cell Helps It Move
Apr 02, 2025
-
Is The Organic Layer On The Top Or Bottom
Apr 02, 2025
Related Post
Thank you for visiting our website which covers about Unauthrized Data Rollbak Or Undo Cia Triad . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
